Technology

Multicentre data collection
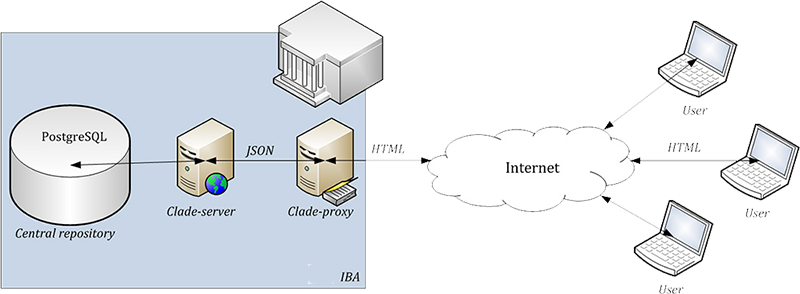
Data are collected in the electronic database, which is based on CLADE-IS robust system. The system has been specifically designed for the collection of large amounts of data in clinical trials and/or clinical registries. It is fully customised to the structure and requirements of the project. The on-line application is accessible to users via any internet browser. Records are stored under a specific identity number (ID) which does not allow any backward identification of any individual patient. The unequivocal identification of patient is only known to the attending physician or to an authorised healthcare professional.
Basic characteristic of the system
- The system is very user-friendly: all data are entered via web forms which are analogical to paper collection (classical CRF).
- The data can be entered into the registry from any computer connected to internet and equipped with a standard web browser that supports encrypted communication between the user and the central database (HTTPS protocol, SSL – Secure Socket Layer encryption).
- No additional software needs to be installed on the client's computer.
- Only authorized persons have access to the registry, using their login and password
- Data in the registry are de-identified, i.e. the patients' records are kept under codes (ID) which exclude any chance that the person might be identified. In this way, the system meets all valid rules on the protection of personal data.
- All data transfer is encrypted in order to prevent a potential abuse during the transfer.
- All submitted data are collected in a central computer - server, where they are safely stored in a database.
Data security
Only authorised users can access the system after entering a valid username and password. The system of user rights is one of key functions in the administration of user accounts. Users can be assigned various levels of authorisation so that they have access to selected functions or parts of the system.
Apart from this, an automatic log-out is done after a predefined period of user's inactivity. This function is aimed to prevent a misuse of an unoccupied computer if the user forgets to log out. Centralised user account management is provided by IBA Helpdesk.
Data are validated on both client and server side. There are also additional validations — any detected problems are reported (queries). Each server is automatically backed up before any changes to the system are carried out (every night). Procedures and safeguards are enforced to ensure that backup data cannot be accidentally overwritten. Latest copies of data from servers are always available in case of an adverse event to ensure a quick resumption of the service. In addition, the system provides an audit-trail functionality, which ensures chronological recording of all activities that have affected registered data.
The security of the IT infrastructure through which IBA provides its data management services is ensured on two independent levels: 1) security of data, 2) physical security of servers.
1. Data security:
- Firewalls. Complete data communication respect rules of central firewall systems on particular locations. Each server has own firewall.
- Encrypted communication HTTPS. Complete data entry is encrypted by protocol HTTPS containing valid and credible certificates.
- Regular backup to remote data storage center. Data from databases are regularly backed up to another location for the case of need or disaster recovery.
- Standby database. Data from database are mirrorred in the real time to an identical database in another geospatial location. In case that primary database is not accessible, it could be manually switched to the second database.
- Redundancy of servers. Web and database servers have their copies permanently online.
2. Physical security:
- Server rooms secured with electronic security system.
- Access to servers controlled with the chip card technology.
- Servers are secured by alarm, detector of fire, temperature detector, move detector and fragmentation detector.
- Nonstop monitoring. Alarm messaging to system administrators via SMS.
All data entered into CLADE-IS passes through several steps of validation. All checks are programmed and validated into the system. This process is performed simultaneously with the creation of the database.
